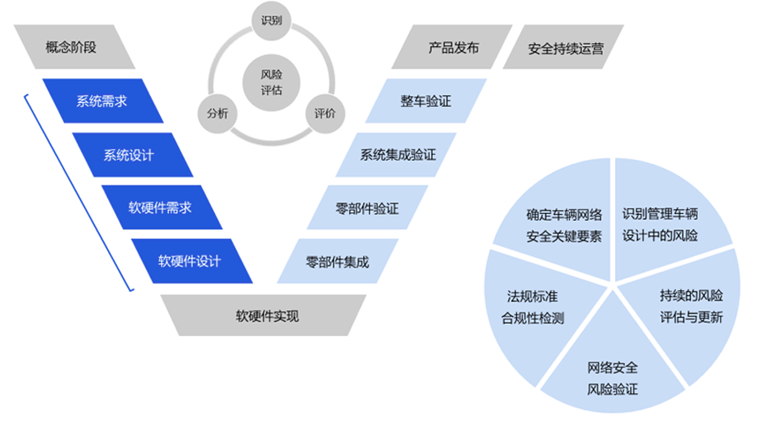
The intelligent connected vehicle information security vulnerability verification platform is used to restore the real vulnerabilities existing in the intelligent vehicle system. By simulating the threat scenario of automotive information security, it realizes the combination of target drones and vulnerabilities to build an attack link platform.
Assist car companies in enhancing their information security capabilities
By using vulnerability exploitation scripts to display the ways in which vulnerabilities are exploited, it has visualization capabilities and can vividly simulate the scenario of vehicles being invaded by networks. It serves as a great help for vehicle enterprises to discover information security vulnerabilities in a timely manner during development and testing, and assists in the construction of their information security capability system.